The data access log allows the application administrator to conduct an audit of access to certain data to determine who and when viewed it.
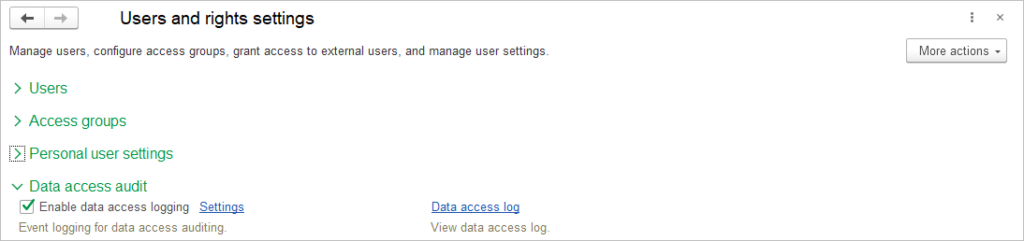
First, you need to set up data access by enabling the checkbox Enable data access logging. Then go to the Settings link.
Next, select the objects you need to track.
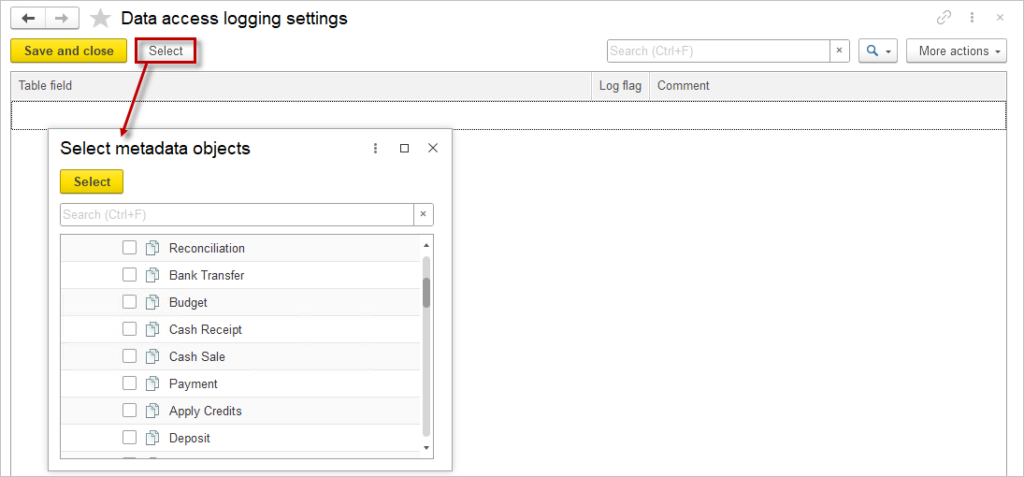
After performing these actions, the application will automatically log who accessed the data and when, displaying this information in red in the Data Access Log.
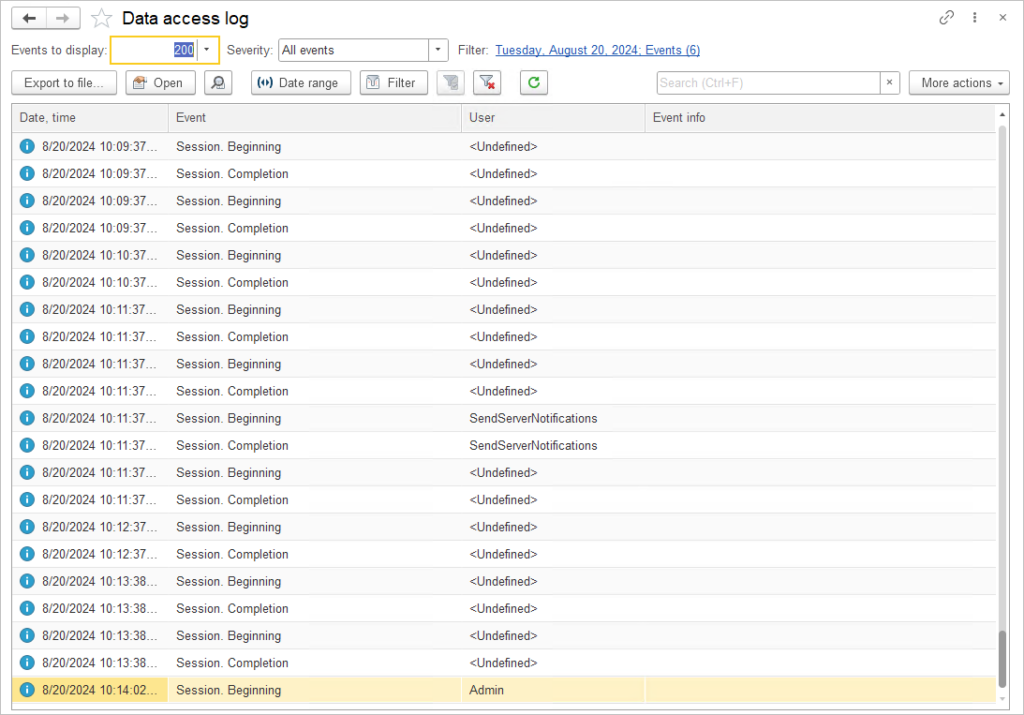
You can use the Filter ![]() button to sort the events and find who made the changes and from which computer.
button to sort the events and find who made the changes and from which computer.
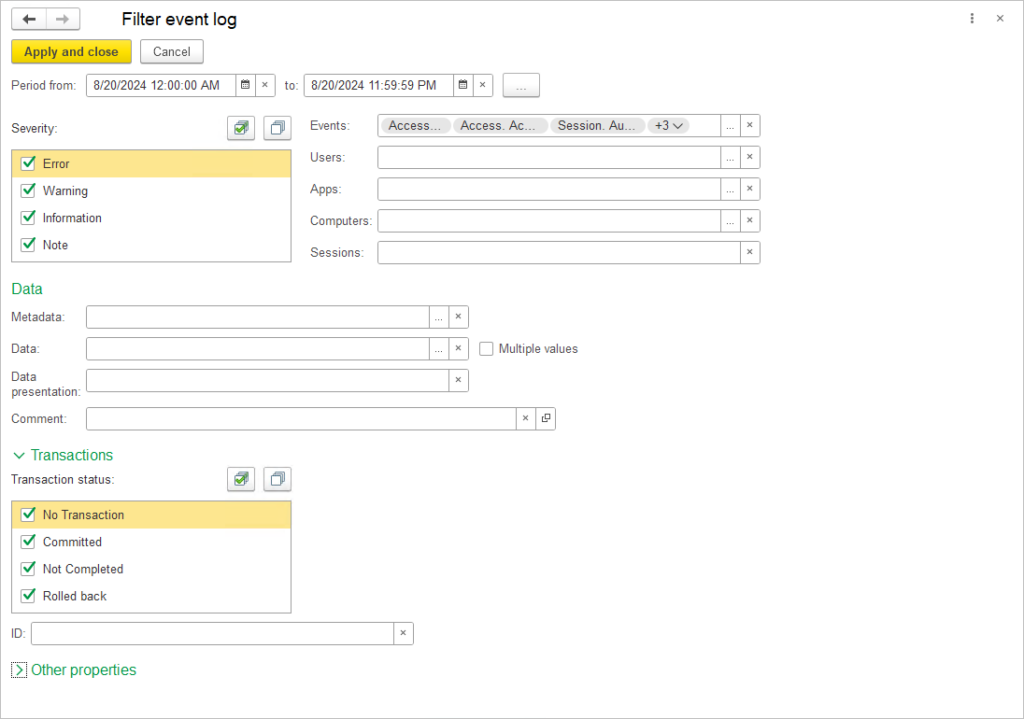
Additionally, if tables or their fields with access control settings were deleted or renamed in the application’s 1С Designer, a pending task to update the settings will appear for the administrator.
