Secure Development with 1C:Enterprise #
The 1C programming language is a high-level, memory-safe language (similar to Java®, C#, or Python) that eliminates common risks associated with manual memory management. Key features include:
- Automatic memory management via garbage collection—developers do not need to handle memory allocation or deallocation.
- No direct memory operations, reducing vulnerabilities such as buffer overflows or memory leaks in application code.
Runtime Security & Stability #
The 1C language executes on the 1C:Enterprise platform, analogous to how Java runs on the JVM. The platform itself is built in C/C++ (like the Java Virtual Machine) and undergoes rigorous testing to ensure reliability:
- Extensive load testing before every release, using real-world applications.
- Proven scalability — recent tests successfully handled 30,000 concurrent users over 10 hours without memory leaks.
- Certified robustness — validated by multiple government certifications for stability and security.
Key Takeaways #
- Developers write applications in a memory-safe language, minimizing risks.
- 1C:Enterprise platform provides a secure, leak-free runtime environment, rigorously tested for enterprise workloads.
User Account and Password Management #
AccountingSuite uses a secure directory services for user account management (authentication, authorization, identity). The application features enterprise-grade security policies like Active Directory, such as:
- Password Complexity: Requires at least three character types (uppercase letters, lowercase letters, numbers, and special characters)
- Password Length: Minimum of 7 characters
- Account Lockout: Protection against brute force attacks
- Password Change Enforcement: Regular password updates required
These security settings are preconfigured for all cloud accounts. For example, the AccountingSuite Portal performs automatic password policy validation during password changes:
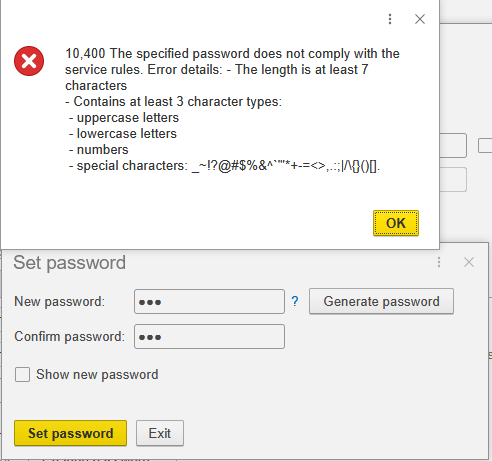
For on-premise deployments, administrators can configure these policies via: Admin Panel → Security Settings → Login Settings

Inactive accounts for 30 days can be detected and alerted both for cloud and on-premise version of AccountingSuite by special plugins and scheduled jobs.
Login and Logoff Process #
Cloud Version
User encodes username and password in order to access the application for cloud version on the login page:
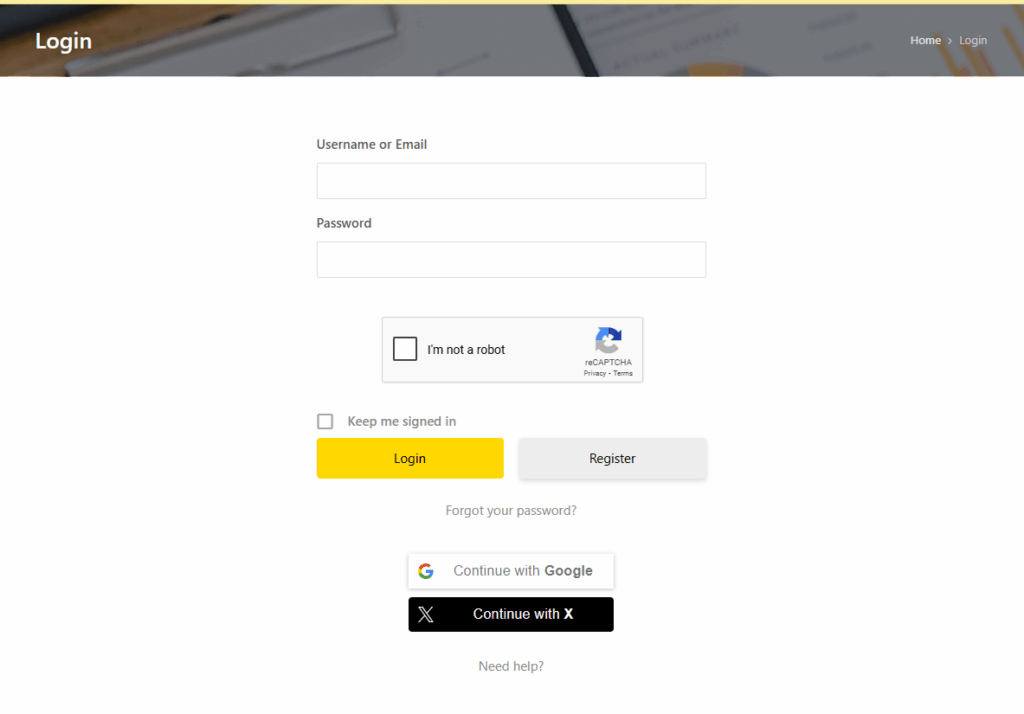
On-premise Version
Authentication occurs via the 1C client interface:
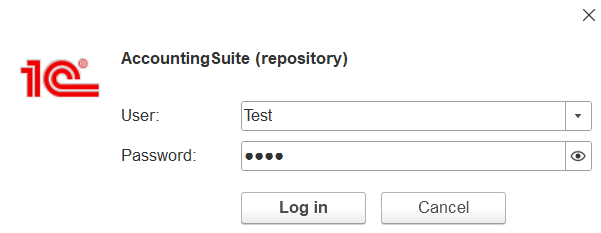
Security Enhancements:
- Cloud: Last usernames are hidden when browsers disable autofill functionality
- On-Premise: Username masking requires Active Directory (or equivalent) integration

Aging of User Account #
AccountingSuite can generate reports of the last successful login of the user through Event log (with Session and User filter):
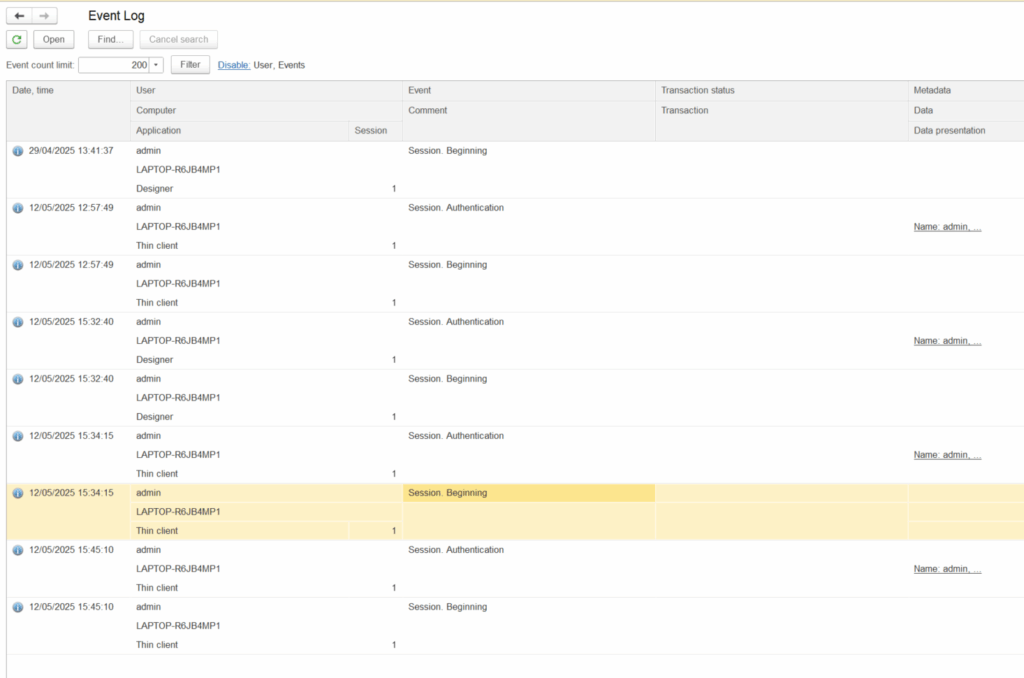
Audit Logs and Monitoring #
AccountingSuite capture audit logs including the following:
- Security logs: (Successfull login, Failed login attempts, Account created, Account deleted, Account enabled, Account disabled, Account locked out).
The information is stored in Admin Panel → Security Settings → Data Access Audit → Data Access Log or using special reports like “User account change history”:
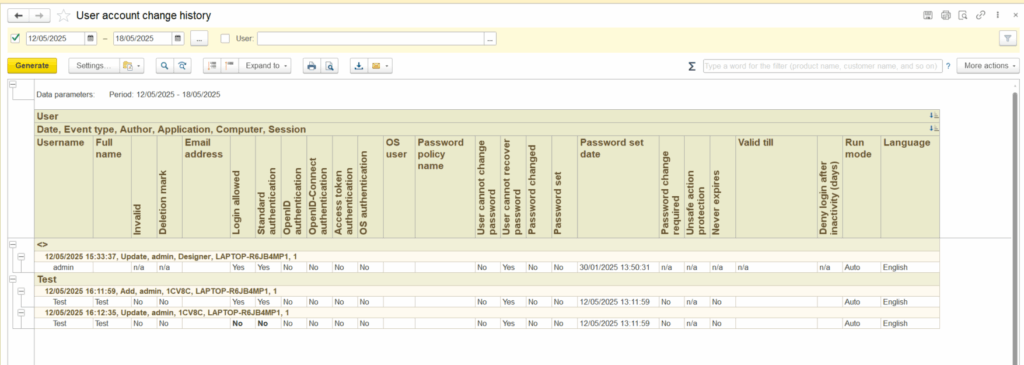
- Application logs: All trasactions including data changes.
This logs can be setup in Admin Panel → Security Settings → Data Access Audit:
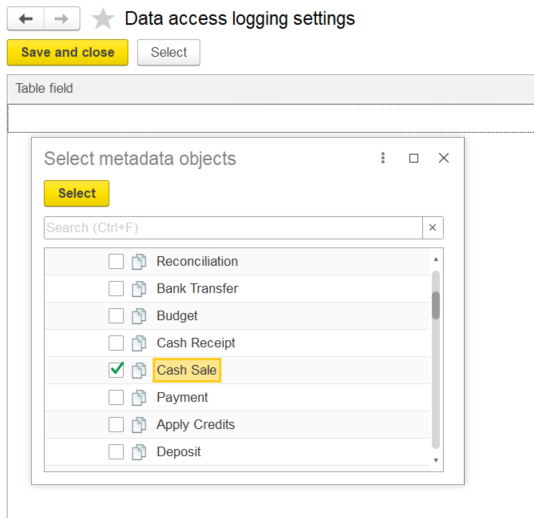
And then analyzed using Admin Panel → Security Settings → Data Access Audit → Data Access Log.
- System logs: (System error logs, System shutdown, Configuration changes).
This logs can be analyzed using Admin Panel → Security Settings → Data Access Audit → Data Access Log filtered by appropriate events. Audit logs can be forwarded/integrated with a third party log monitoring system.
Session Management #
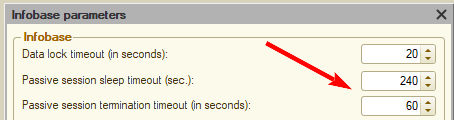
- AccountingSuite can be set up to log out user resulting for the user to repeat login attempt upon reaching a maximum of 15 minutes of inactivity using configuration Administration → Infobase Parameters, “Passive session termination timeout” parameter:
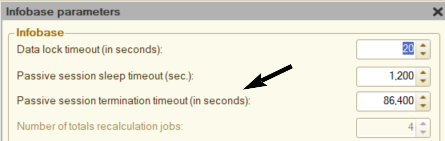
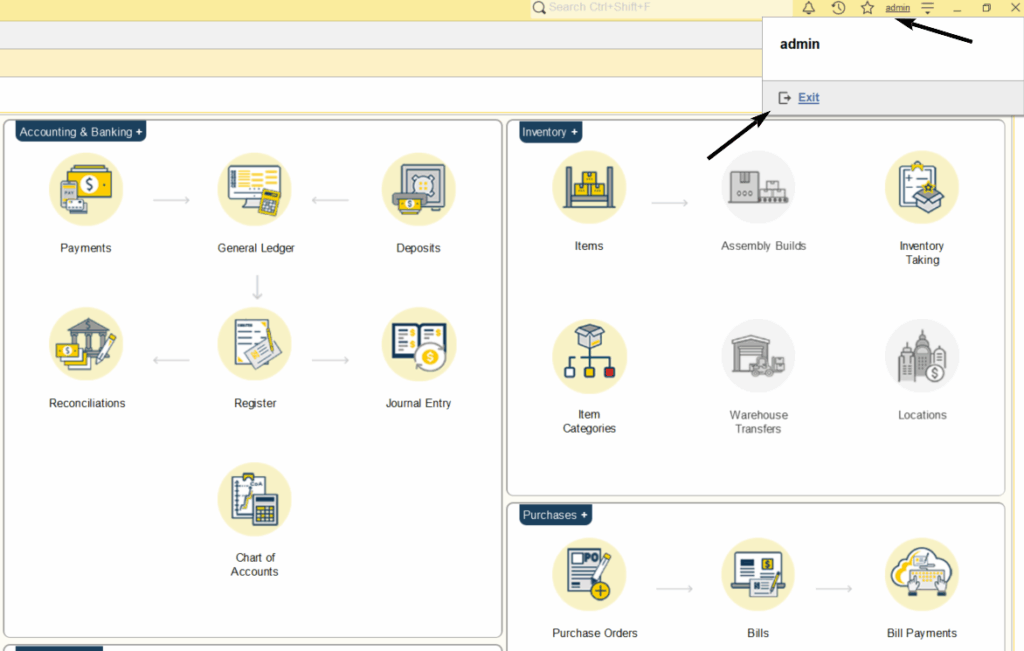
- Users can explicitly terminate their session with logout button by clicking on the user’s name at the left corner of the window, and then on the Exit:
- User is automatically logout when the window session is close (you need to use thin client for this option)
- User logins again if the application/session window was closed without proper logout (you need to use thin client for this option)
Simultaneous login #
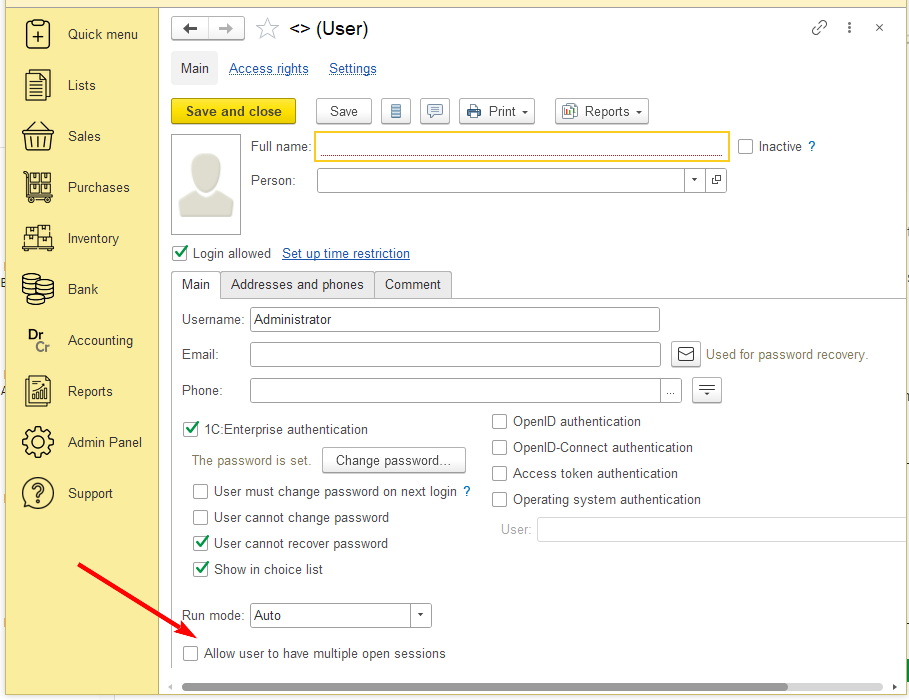
AccountingSuite prevents simultaneous logins by restricting users to one active session per account. Administrators can manage this restriction in the user setting:

Please note: For on-premise deployments, issues with stale sessions from improper logoffs can often be resolved by reducing the session timeout values. We recommend starting with a 240-second sleep timeout and a 60-second termination timeout for passive sessions.
Default Administrator Accounts Turn Over and Database Cleanup #
Users create their own credentials during initial setup, eliminating the need for administrator-managed account turnover. The system generates an empty database that users configure upon first launch.
Interface and Component/Module Access #
AccountingSuite offers customizable role-based access control, allowing administrators to precisely configure which interfaces, components, and modules each user can access according to their assigned privileges
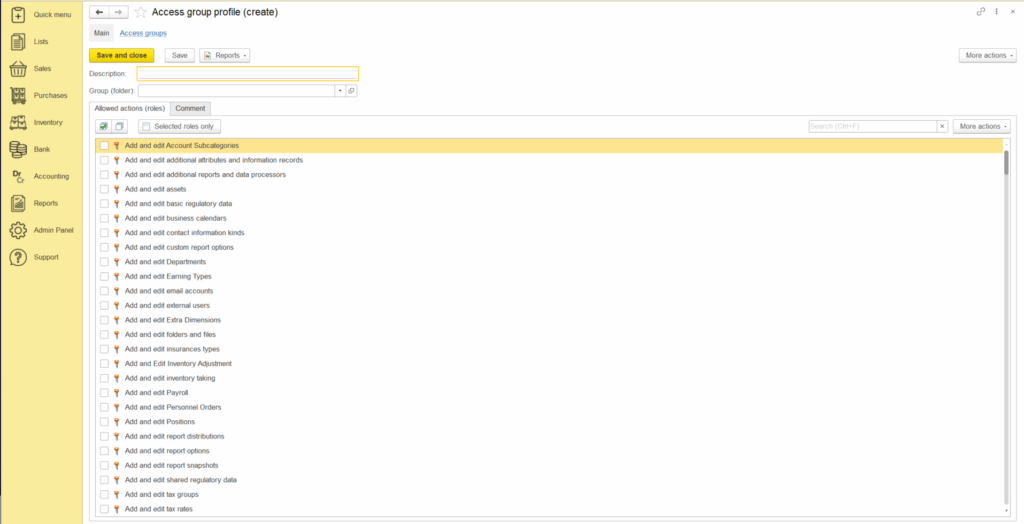
Source Code Turn Over #
AccountingSuite is an open-source application. Users can review the source code directly by launching the software in configuration mode.
User Access #
AccountingSuite provides granular access control tailored to each user’s role and job function. With over 350 predefined roles, the system precisely defines permissions for adding, editing, and viewing various objects and interfaces. These roles can be combined into customized profiles and role groups, enabling administrators to efficiently map permissions to specific organizational functions:
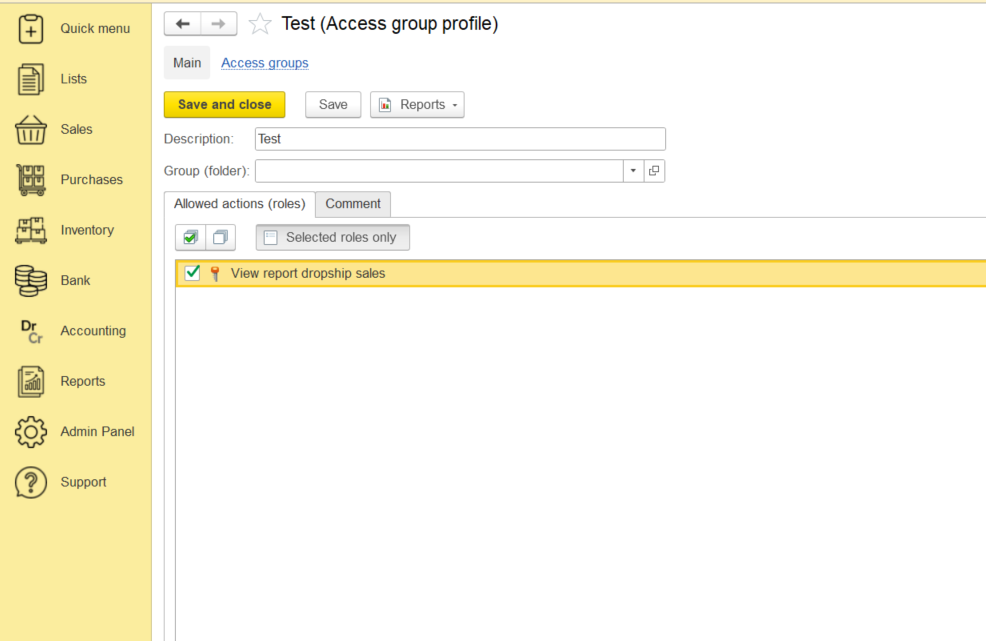
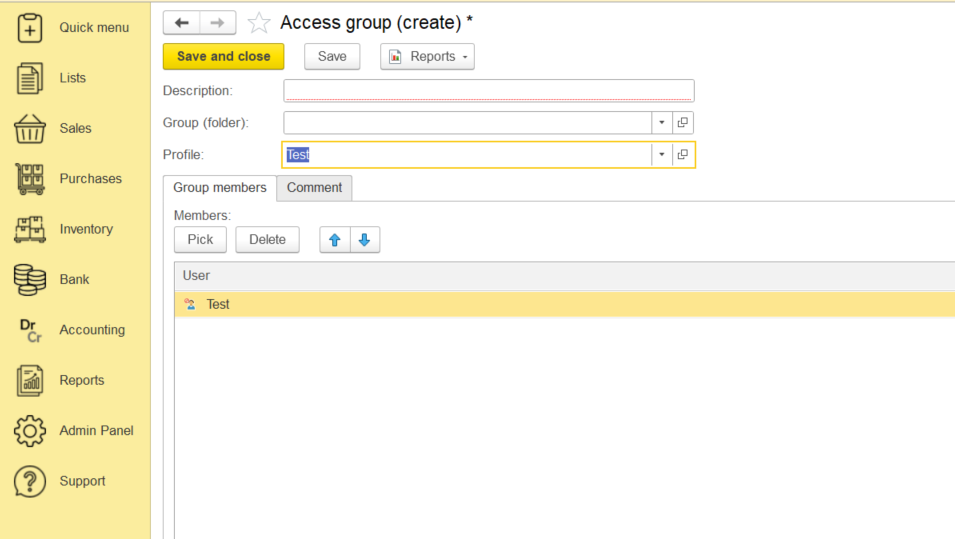
Access of users to transactions or information can be limited to scpecific roles such as but not limited to: Accounting, Cash Operation, Marketing, etc.
Approval Process #
All completed transactions can be reviewed and approved through the Admin Panel under Security Settings → Data Access Audit. For enhanced control, administrators can implement detailed maker/checker workflows using the configuration extensions feature.
Vulnerability Assessment #
AccountingSuite and its supporting software receive regular security updates to patch vulnerabilities and protect user data.
Encryption #
AccountingSuite integrates with third-party encryption solutions like Microsoft CryptoAPI through its built-in CryptoManager. This supports industry-standard encryption algorithms including AES-128, 3DES/TDES, and ECC for robust data protection:
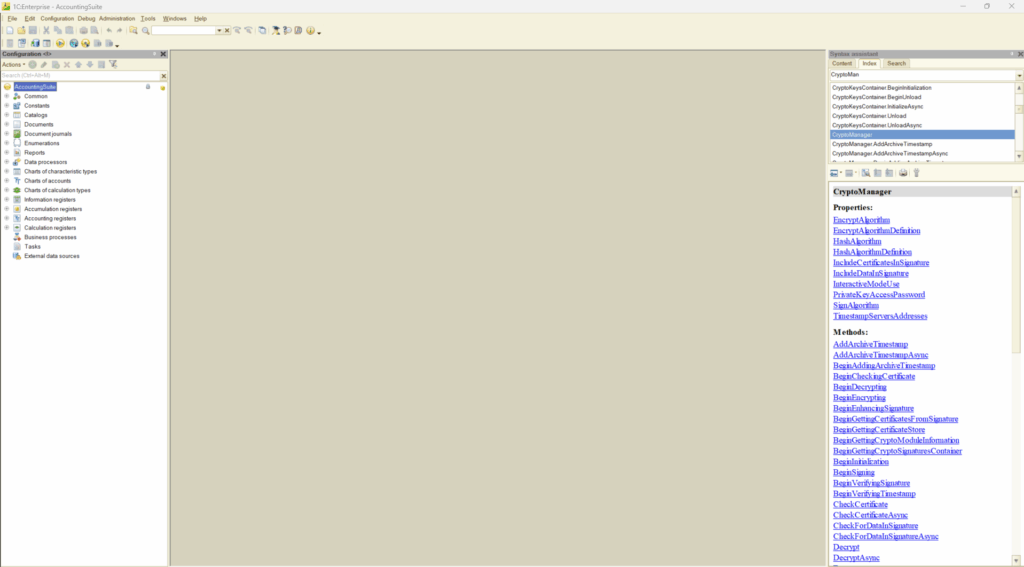
All sessions are secured against eavesdropping via standard TLS/SSL encryption for web clients and cloud deployments of AccountingSuite. For on-premise installations, equivalent protection can be configured in the Administration Console under infobase settings.
Note: This may not be necessary for fully trusted local networks, as enabling encryption can reduce data transmission speeds.
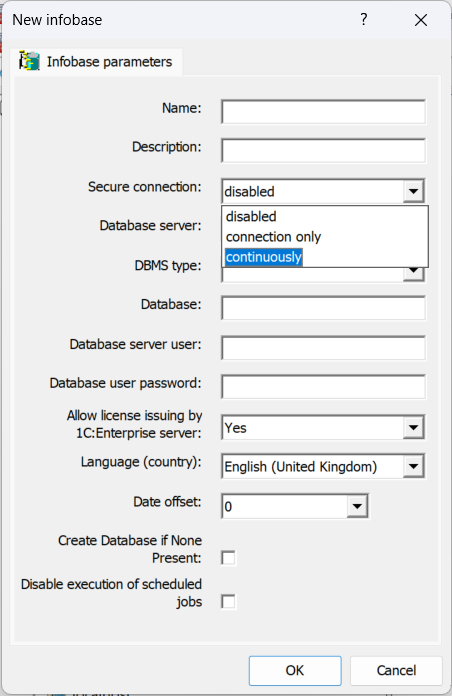
Administrator’s role #
AccountingSuite is able to provide two (2) different Administrator’s roles for the issuance of access:
- Role 1 (UpdateDatabaseConfiguration). Administrator can only create/define the role of the users accessing the application. NO access rights for the issuance of access to the users
- Role 2 (EditAccessGroupMembers). Administrator can only issue/grant access to the users. NO access rights to create or define the role of the users.
